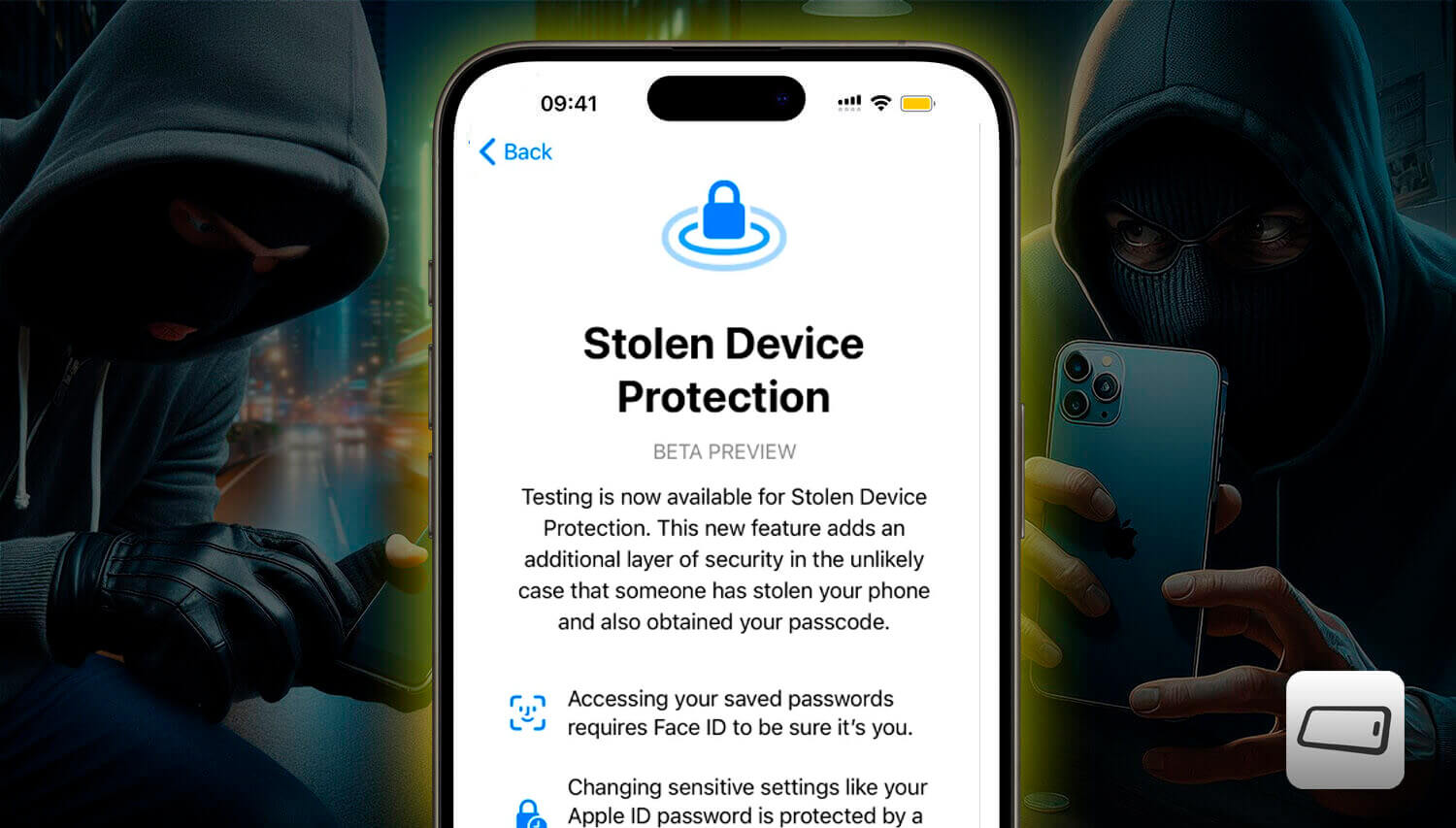
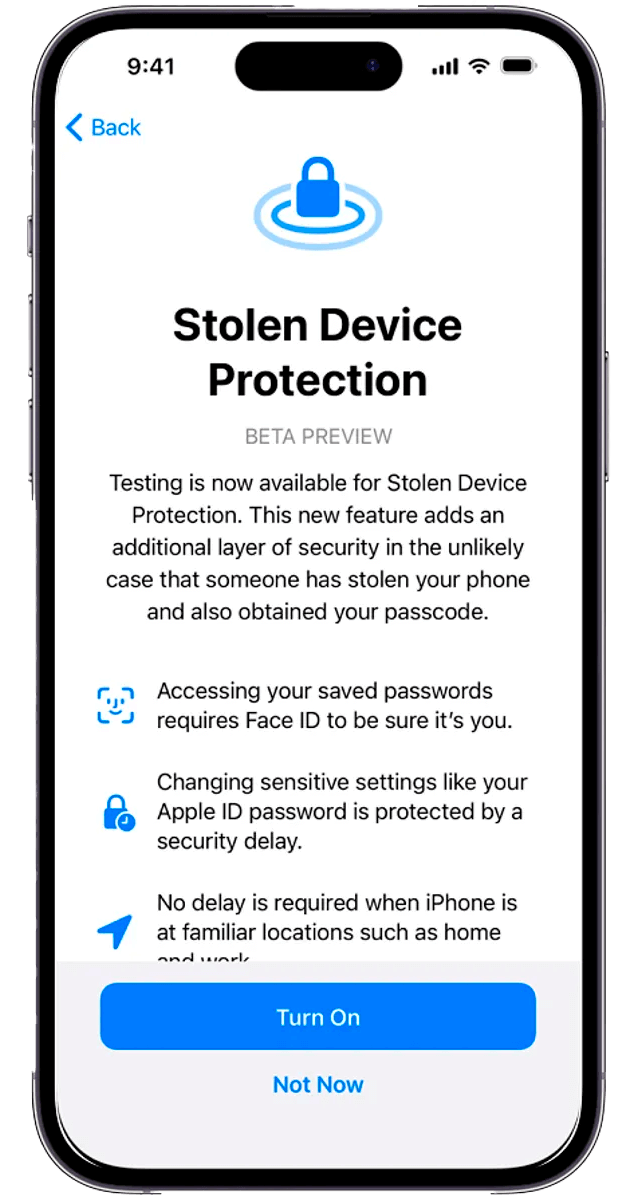
Apple is introducing a new security feature in iOS 17.3, called “Stolen Device Protection“, designed to provide an additional layer of security for iPhone users.
The feature is currently in the testing phase in the developer version of the operating system.
Understand how the feature will work and what Apple is doing to make it as difficult as possible to access your data in the event of theft or loss of your iPhone.
How it works today
The iPhone has long had good data protection for customers. However, there is a problem: if the thief knows the device password, they can even change your iCloud password.
And let’s face it, it’s not very difficult for a criminal to access this. They just need to have seen you from a distance typing the code, or forcing you to provide it during the theft.
There is another aggravating factor. Nowadays, there are brute force devices capable of discovering less complex passwords in a matter of hours or even minutes, allowing the thief to access all your data.
Biometric recognition for restricted access
The main feature of Stolen Device Protection is the requirement of biometric information from users, such as facial scanning or fingerprints, to access critical phone functions.
This includes the ability to change the Apple ID password or disable Face ID.
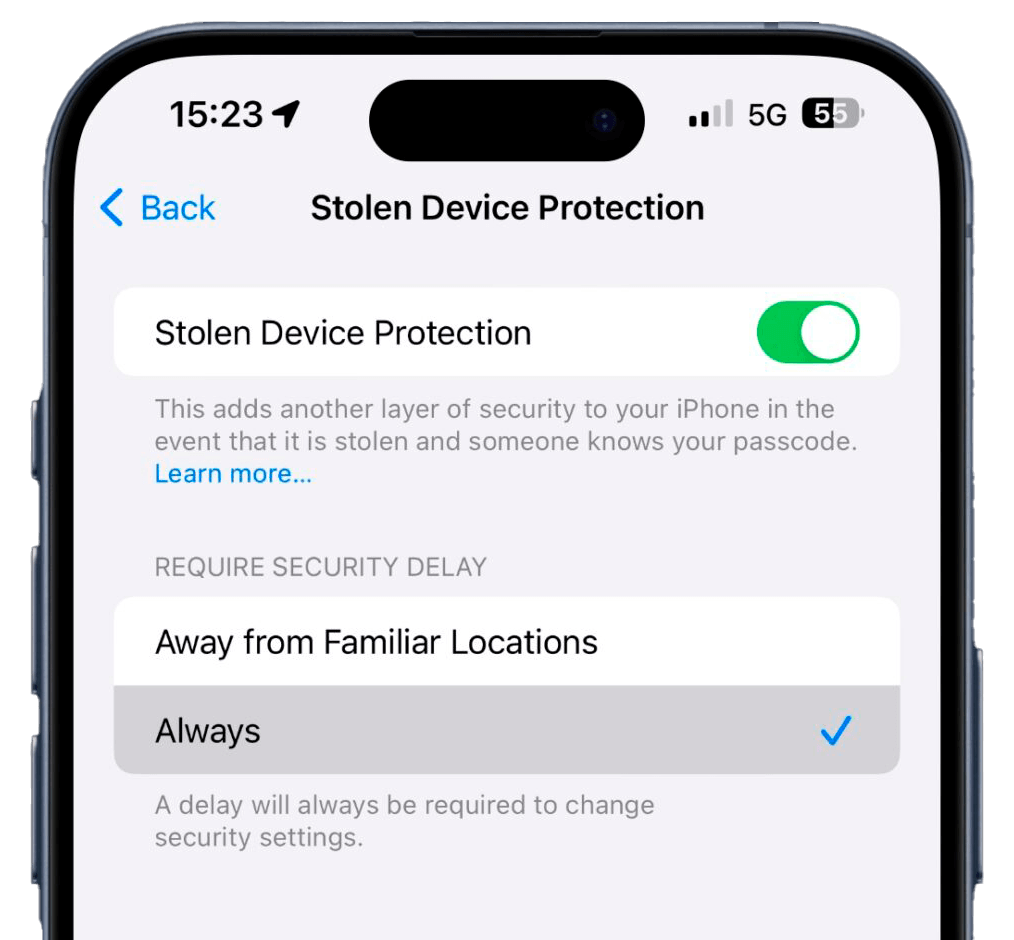
However, this protection activation occurs when the device is in an unknown location.
Three additional security layers
Once enabled, the feature establishes three additional security barriers:
- The first requires facial authentication to access passwords saved on the device. This measure is particularly crucial as Face ID is used in a variety of services, including payments via Apple Pay.
- The second layer of protection consists of an intentional security delay. If a malicious individual gains access to the device’s unlock code and tries to change the Apple ID credentials, Apple will impose a delay to allow the original user to intervene. This is designed to prevent unwanted activities in case of theft.
- The third barrier allows the user to remotely remove all content stored on the iPhone in case of loss or theft, using a trusted device. This measure is an additional safeguard to protect sensitive data.
How to enable Stolen Device Protection
Activating Stolen Device Protection in iOS 17.3 is a simple process.
Users need to ensure they are using the specific version of the operating system (iOS 17.3) and then access the settings, select “Face ID and Passcode” and enable the stolen device protection option.
This feature is already available for all iPhones with the system starting from iOS 17.3.